The first line of defense for any device or system on a network is the network itself. Following security best practices for endpoint and perimeter security is the foundation of data security. When properly configured on a secure network, TrueNAS further protects your data from security risks.
TrueNAS continues to receive new and enhanced security features and tools with each release. TrueNAS Enterprise, as well as the free open source TrueNAS editions, are becoming increasingly sophisticated in protecting data from a wide variety of threats. Also, more users are deploying TrueNAS to meet retention and reporting requirements for compliance. To build on this foundation, we are introducing TrueSecureTM, an optional FIPS 140-validated crypto module for TrueNAS Enterprise appliances and launching the updated TrueNAS security site.
Secure by Design
Storage vendors at the lower end of the market, like QNAP and Synology, have made some design decisions that favored ease of use over security which have subjected their users to continual virus and ransomware attacks. By contrast, enterprise storage products like TrueNAS must be built with security as a primary design principle so that they can integrate into secure network environments and minimize attack vectors against data.
However, new threats come online with such frequency that new features and tools will always be needed to stay ahead of the curve. With TrueNAS SCALE 22.12.3, we introduced a FIPS 140-3 validated crypto module and the option to enable TrueSecure on Enterprise appliances.
New Security Page Provides Enhanced Protection
Infrastructure and data can be better protected with knowledge of all vulnerabilities. The updated TrueNAS Security site now includes a detailed Software Bill of Materials (SBOM) for TrueNAS and provides detailed documentation on all known security vulnerabilities and CVEs. This is done with regular and automated security auditing. Please explore the information which also provides links to the relevant Open Source repositories and planned fixes.
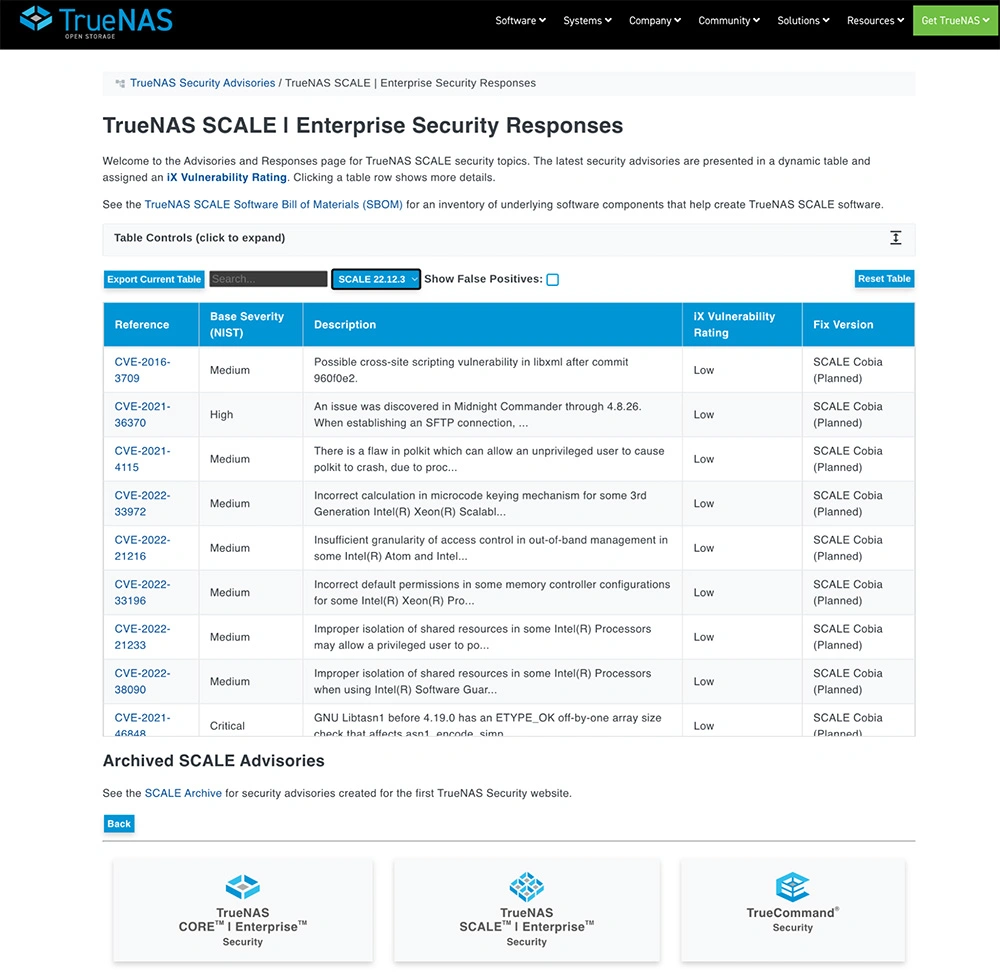
TrueNAS Security Features are Extensive
In a short blog, it is impossible to explain every feature under the umbrella of “security” and why each is important. With ransomware being top of mind in 2023, security features specific to ransomware protection are summarized in this recent blog. The chart below tries to capture the key categories of security-related features in TrueNAS. If you need more information, visit the TrueNAS Security site.
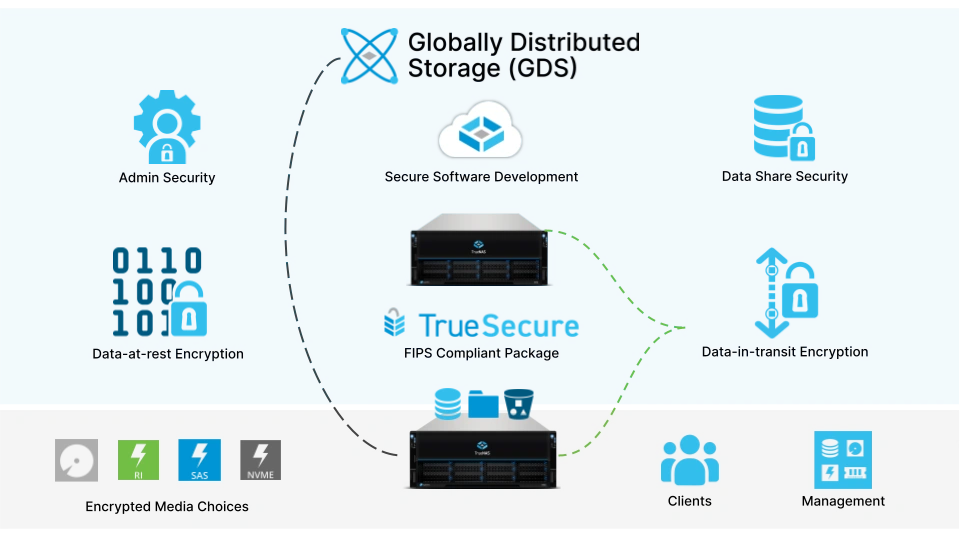
No amount of storage-level security will make up for not following network and general IT best practices. For example, we do not recommend directly attaching TrueNAS to the Internet without a robust firewall. Services like Active Directory and LDAP are also recommended for password administration. By following network security best practices, TrueNAS is more secure.
Backdoor access to storage is an attack vector that concerns users around the world. Whether left vulnerable by a public sector organization or a private business, backdoor access represents a target for both state-sponsored and private malicious actors. TrueNAS can be configured to strictly control access, and unlike proprietary storage vendors, all of the software that enforces those controls is open and reviewable.
TrueNAS SCALE Bluefin Enhances Security
With TrueNAS SCALE Bluefin’s release last year, there have been many security advancements:
Rootless administration allows changing away from using the commonly known “root” username and instead setting up your own unique administrator usernames and passwords.
OpenZFS snapshot retention tags can prevent snapshots from being deleted, remaining on the system permanently as a restore point. This provides additional protection against ransomware by allowing the administrator to make a decision on when it is safe and appropriate to remove the snapshot outside of normal retention policies.
API Keys with ACLs are laying the groundwork for future Role-Based Access Control (RBAC) enhancements in coming releases. This allows further fine-grained control over assigned API key privileges.
2-Factor Authentication (2FA) verifies the identities of administrators using Google Authenticator or any Time-based One-Time Password (TOTP) compliant authentication application. This feature also exists in TrueNAS 13.0.
iX-Storj Globally Distributed Storage is primarily cost-effective cloud storage, but it inherently protects data by encrypting it on the TrueNAS system before distributing the data via erasure coding over a global network. Thanks to the combination of zero-trust and zero-knowledge encryption in use, no storage provider or government entity has access to your private data stored on iX-Storj, so your data remains yours alone.
Introducing 
Government agencies often require specific security and compliance measures in both software and hardware which are not normally required in other businesses. TrueSecure is an optional package available in TrueNAS Enterprise (SCALE 22.12) that delivers specific benefits to Government organizations. Our goal is to comply with the requirements of the NIST Cybersecurity Framework and make this additional security as cost-effective as possible. These capabilities are also the basis of international support for ISO 27001.
Many security capabilities will find their way into TrueNAS, but some of these will be specific to TrueSecure. TrueSecure provides the following capabilities:
FIPS 140-2 validated storage media provide highly secure Data-at-Rest capabilities. Both HDD and SSD (SAS or NVMe) drives can be provided on standard TrueNAS Enterprise systems. These drives are similar to self-encrypting drives (SED) but include tamper-proof mechanisms for additional security.
FIPS 140-3 validated software encryption module provides highly secure Data-in-Transit capabilities. The validated encryption algorithms are more secure than the current open source algorithms and validated for use in critical Federal use-cases. For example, these algorithms will protect administration and data replication tasks.
Key Management Interoperability Protocol (KMIP) provides the capability to centralize the management of SED and ZFS encryption passwords for larger organizations. This capability is also in TrueNAS Enterprise 13.0.
With TrueSecure, iXsystems is actively working to maintain NIST 800-171 Compliance, which is the preferred approach for USA Government entities to manage their cybersecurity. It is a comprehensive and well structured approach that iXsystems is adopting, along with the TrueNAS product requirements. Any additional capabilities needed are being added to TrueSecure, if not in the general TrueNAS products. iXsystems is also developing Security Technical Information Guides (STIGs) for use with TrueSecure to help lockdown TrueNAS Enterprise systems and ensure secure operation.
TrueNAS Enterprise 22.12 is not only secure storage, it can be configured for government-grade security. With the Cobia release later in 2023, new features and tools will continue to enhance security. Areas being actively invested include file change auditing, virus scanning, and additional ransomware prevention. Stay tuned for more information which will be available as Cobia enters its BETA phase in Q3.
